Lecture 4
RISC-V Instructions
Lecture
Outline
- Stored program concept.
- Memory layout.
- RISC-V ISA base and extensions.
- Instruction encoding (R, I, S, SB, U, and UJ formats).
Workshop
Outline
- Discuss the tasks from the previous seminar.
- Get familiar with the RISC-V ISA Specification (instruction types, encodings, etc.).
- Practice with encoding and decoding instructions.
- Get familiar with pseudoinstructions.
- Understand the use of labels and branch instructions.
- Practice writing programs with conditions and loops.
Tasks
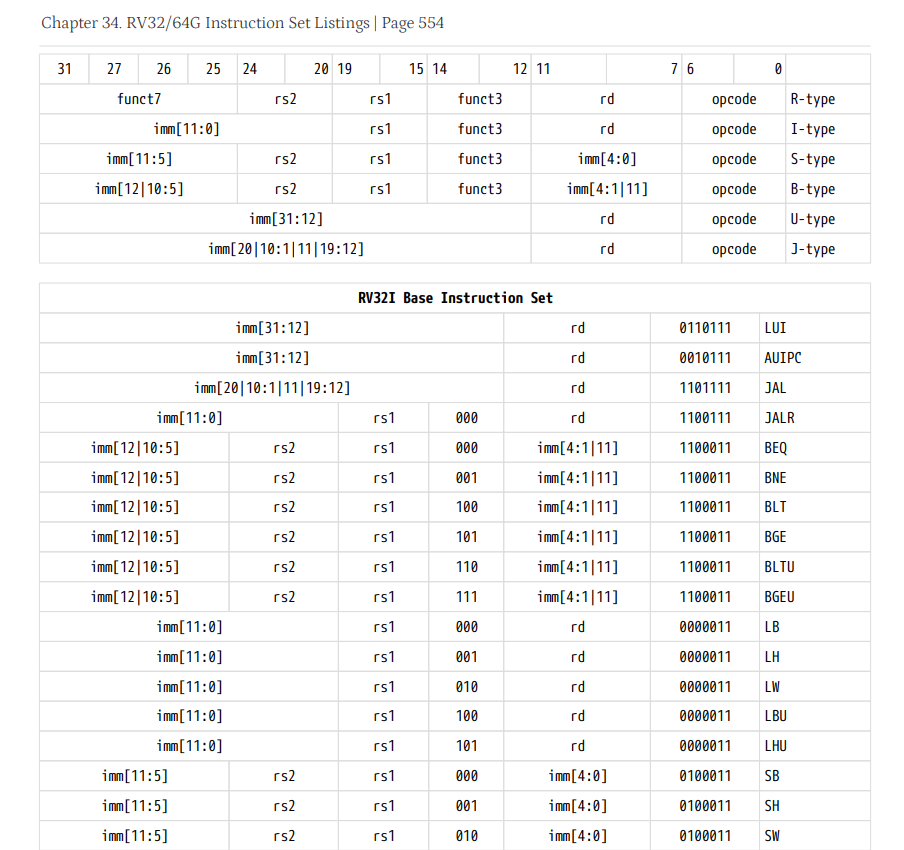
See “Chapter 35. RV32/64G Instruction Set Listings” (page 608, pdf page 628) of document “The RISC-V Instruction Set Manual Volume I” to get instruction encodings.
-
Encode the following instructions to the binary format (see the rules in the ISA specification):
-
R-type:
add t3, t1, t2 -
I-type:
ori s0, t1, 0x123 lw t1, 0x8(t0) -
S-type:
sw t1, 0x8(t0) -
SB-type:
beq t2, t3, 16 beq t2, t3, -8 -
U-type:
lui t0, 0x12345 -
UJ-type:
jal zero, 16
-
-
Decode the following hexademical values to instructions:
0x98765437 0x00744433 0x0080006f 0xfff37293 0x00000463 0x00032823 -
Get familiar with RISC-V pseudoinstructions (
mv,li,la,b,j, etc). What instructions are used to replace them when a program is assembled:mv t0, t1 li t0, 0x12345678 li t0, 16 b label j label la t0, labelNote: Add
labelto some place in your code. See what code will be generated in theExecutepanel of RARS. -
Write a program that inputs an integer value
xand prints-1if it is negative,0if it equals0, and1if it is positive.One of possible solutions is this:
main: li a7, 5 ecall mv t0, zero beqz a0, done li t0, 1 blt zero, a0, done li t0, -1 done: li a7, 1 mv a0, t0 ecallPropose any other solution?
-
Write a program that inputs two integer values
xandyand prints first the smallest of them and then the largest of them.
Homework
Decompile the machine-level program provided below. Convert instructions from the hexadecimal representation into assembly source code. Put the source code into RARS, assemble and run it. Ensure that the code is identical to the one provided below (see the picture.
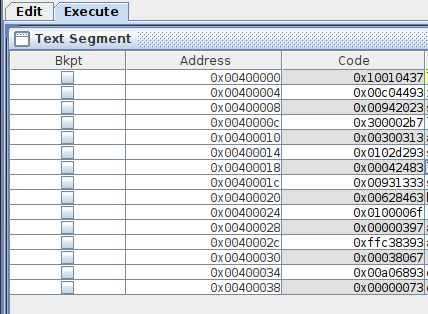
Submit the resulting assembly text into Ejudge (task “RiscvEncoding1”).
0x10010437
0x00c04493
0x00942023
0x300002b7
0x00300313
0x0102d293
0x00042483
0x00931333
0x00628463
0x0100006f
0x00000397
0xffc38393
0x00038067
0x00a06893
0x00000073
References
- Machine Language. Section 6.4 in [DDCA].
- RISC-V Technical Specifications (official standards).
- The RISC-V Instruction Set Manual. Volume I: Unprivileged ISA (ongoing drafts).
- Opcode (Wikipedia).
- Addressing Mode (Wikipedia).
- C++ library for RISC-V instruction encoding (for illustration).
- Formal specification of RISC-V ISA (for illustration).